The news media is now swirling in reporting ransomware attacks; of course, the ransomware attacks did not begin with the Colonial Pipeline attack; the attack that shut down oil and gas delivery to the East Coast. Colonial Pipeline, as part of the critical national infrastructure, is responsible for delivering about 45% of the fuel the East Coast uses; this includes gasoline, diesel, heating oil, and aviation fuel, which is about 100 million gallons of fuel a day. The after-action report (AAR) will no doubt highlight the cause or entry point of the ransomware attack. The expectation is that the impending AAR will describe how the exploit took advantage of the company’s poor cyber hygiene, meaning the company’s systems were out of date, poorly configured, they were using poor passwords, there was a lack of segmentation, etc. Recall the SolarWinds CEO Sudhakar Ramakrishna testified that the hack was mainly due to poor password control. The use of “solarwinds123” as the password, in use since 2017; it was most likely not an out-of-control intern.
In 2012 Congress struggled to pass legislation directing the Secretary of Homeland Security, owners and operators of critical infrastructure, the Critical Infrastructure Partnership Advisory Council, federal agencies, and the private sector to assess cybersecurity risks; designate critical infrastructure; develop risk-based cyber performance requirements; and implement cyber response and restoration plans. This was the watered-down version of the original bill. The bill was attacked by the US Chamber of Commerce, the operators of critical infrastructure, and some of the private sector companies. The reason for the pushback was it was going to cost too much, it was over-regulation, it was burdensome when these entities were enacting industry best practices.
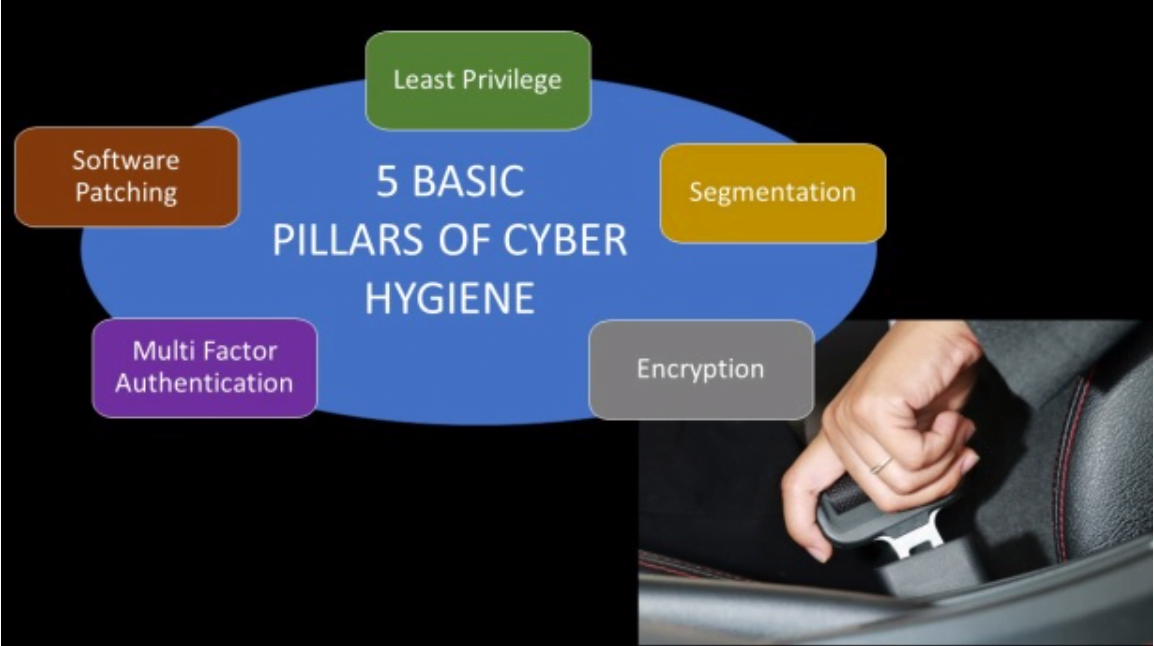
This brings to mind the great automobile seatbelt battles of the 1970s and 1980s. Today getting in your car and putting on a seatbelt is almost a subconscious act. Today seatbelts and airbags are standard, like a car radio and air conditioning. Though seatbelts were first developed in the 1890s, it took until 1968 when the Motor Safety Standard went into effect that required all vehicles to be fitted with, essentially, a lap belt. The battles for enforcement were at both the state and federal levels, where the automobile manufacturers, business organizations, and legislatures battled against this regulation as over-regulation, costly, intrusive, burdensome, and un-American. Today someone not using the standard three-point seatbelt is considered irresponsible; today, you cannot buy a new car without seatbelts and airbags; and of course, by miles driven, driving a car has never been safer.
There is hardly a week that now goes by without some report of a cyber-attack against a business or government agency. The Colonial Pipeline attack is not unusual; government agencies are also attacked. A medium-size police department was attacked twice in the last few years; the second attack was a ransomware attack initiated through an employee downloading malware-infected email. This resulted in two effects; the first was the exfiltration of police records and other personally identifiable information; the second was the encryption of their data resulting in the ransomware attack. When the police department did not pay the ransom, the exfiltrated data was released on the dark web for all to see. The release of the data then is another cascade of problems and issues, as the effect of this information in the public impacts many thousands in a greater number of ways.
Despite the efforts of industry associations, business organizations, and individuals, cybersecurity requirements are going to be the rule, not the exception. Secondly, these regulations will bring along the requirements for certification, meaning someone will check your work. The self-attestation model has proven to be less than successful. For the most part, cyber hygiene, which is the basic level requirement, is like putting on your seat belt. These are simple things that most can do without a high degree of skill.
The baseline for good cyber hygiene is things like making sure your system software is up to date; for this, you can turn on the automatic update function. Ensuring you have antivirus software, that is turned on, it is automatically updated, and it should periodically scan your system. Other actions are long, complex passwords, which means ten or more combinations of characters, letters, numbers, etc. There should be the separation or segmentation of data access; there should be no universal access to anything. Another one is multifactor authentication (MFA); this too is an extra step, like putting on a seatbelt. The adage is to prepare for the worse, and that would be to have a backup for your system that is air-gapped. This means the system backup is not connected to your system; it is disconnected, it is air-gapped. In this way, if there is an attack, you may lose all of your data. However, you will recover from the air-gapped backup; you will only lose the data that was not on the drive.
As we all know, people are resistant to change or anything new, even when it is in their best interest, think of seat belts. The cost to invoke layers of cybersecurity and system security protections has been the main reason for pushback. After these attacks and the massive costs of recovery, the expense in prevention has been demonstrated to be less than the cost for recovery. The advice is to then begin putting into place the basics of good cyber hygiene.

